In this article I will share walkthrough to solve access control vulnerability labs in portswigger academy.
Lab 1: Unprotected Admin Functionality #
Overview #
This lab contains an unprotected admin panel. Our goal is to delete the user carlos to solve the lab.
Solution #
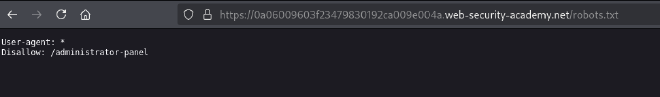
- Access the
robots.txtfile to find the admin panel link:
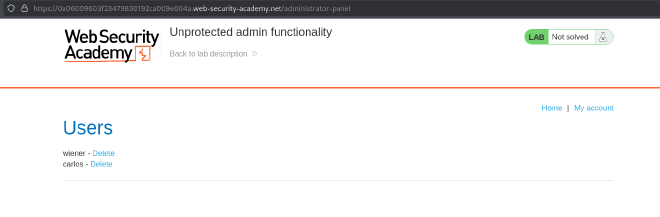
- Navigate to the admin panel URL and log in without credentials.
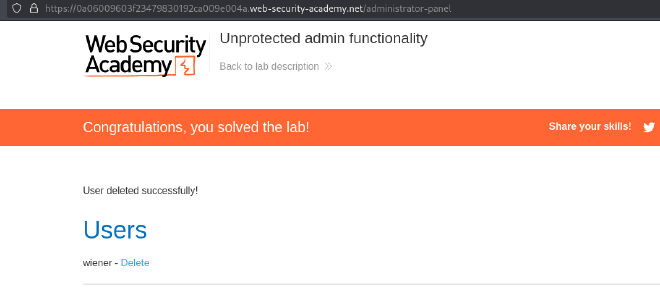
- Delete the user
carlosto complete the lab.
Lab 2: Unprotected Admin Functionality with Unpredictable URL #
Overview #
This lab’s admin panel is at an unpredictable location disclosed in the application. The goal is to delete the user carlos.
Solution #
- Inspect the product page source code to find the admin panel URL:
var isAdmin = false;
if (isAdmin) {
var adminPanelTag = document.createElement('a');
adminPanelTag.setAttribute('href', '/admin-061w6y');
}
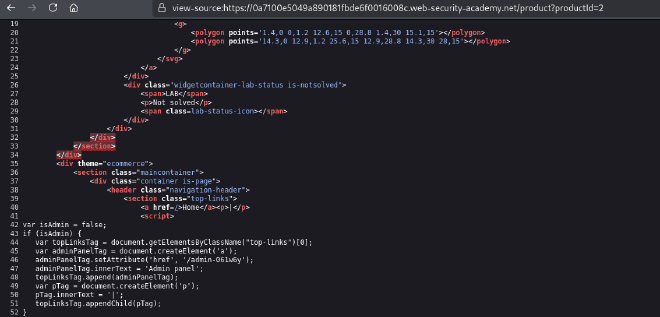
- Navigate to the admin panel and delete carlos.
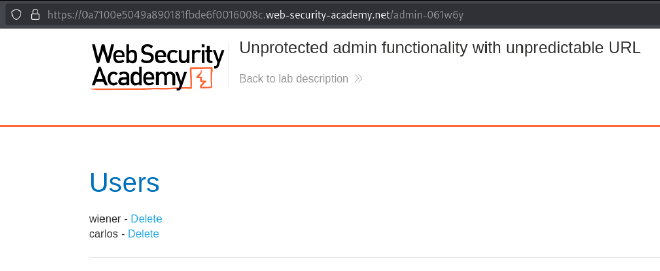
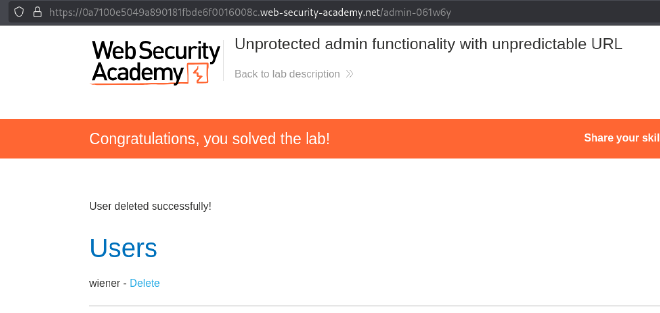
Lab 3: User Role Controlled by Request Parameter #
Overview #
This lab uses a forgeable cookie to identify administrators. The objective is to access the admin panel and delete carlos.
Solution #
- Log in with the provided credentials:
Username: wiener
Password: peter

- Inspect the request headers. Note the Admin cookie:
Cookie: Admin=false; session=Jiu7Q6cGNKF9NY0sL1GV75R1Un3Zrqk4
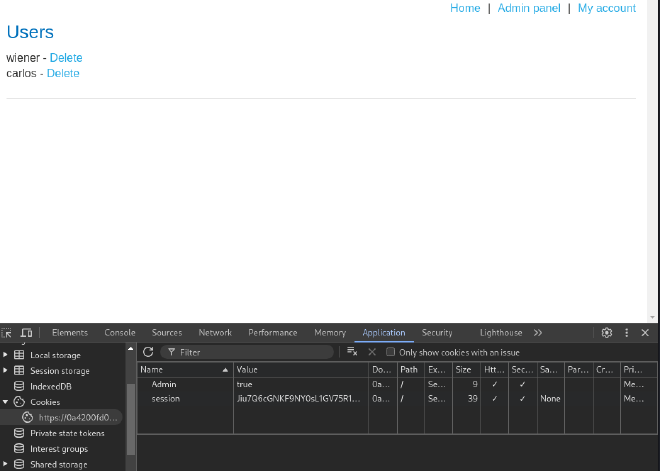
- Modify the Admin cookie to true using Burp Suite:
Cookie: Admin=true; session=Jiu7Q6cGNKF9NY0sL1GV75R1Un3Zrqk4
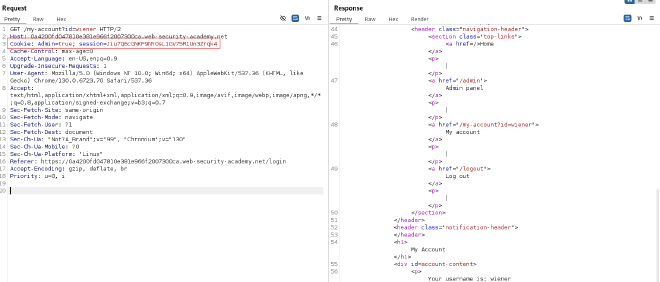
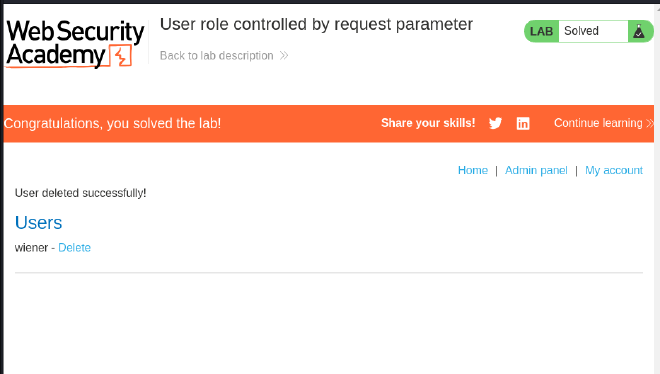
- Modify the Admin cookie to true in browser and refresh to access admin panel and delete
carlos.
Lab 4: User ID Controlled by Request Parameter with Unpredictable User IDs #
Overview #
This lab requires escalating privileges by identifying carlos’s GUID and submitting his API key.
Solution #
- Log in using the provided credentials:
Username: wiener
Password: peter
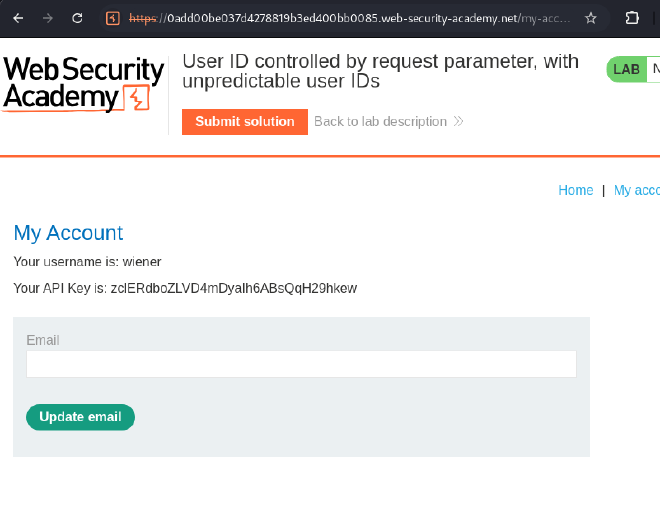
- Inspect your account page to find your API key.
- Find carlos’s GUID by inspecting his blog posts:
https://0add00be037d4278819b3ed400bb0085.web-security-academy.net/blogs?userId=6edbadd6-1268-4466-83f9-0dbebb148cad
- Use Burp Suite to request carlos’s API key:
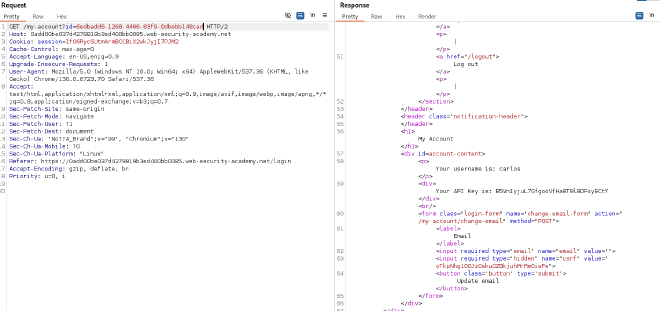
- Submit carlos’s API key to complete the lab.
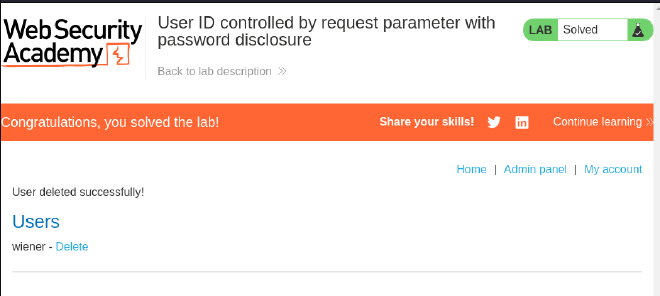
Lab 5: User ID Controlled by Request Parameter with Password Disclosure #
Overview #
This lab involves retrieving the administrator’s password by manipulating the id parameter, then deleting carlos.
Solution #
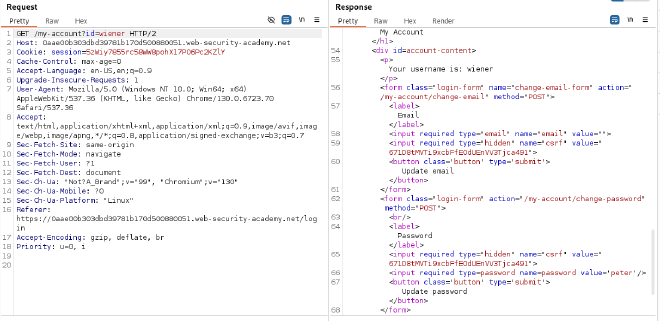
- Log in using the provided credentials:
Username: wiener
Password: peter
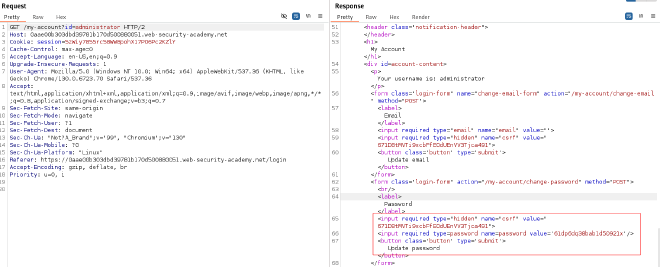
- Inspect the request for the account page. Modify the id parameter to
administratorusing Burp Suite and retrieve the administrator’s password from the response:
GET /account?id=administrator
- Log in as the administrator:
Username: administrator
Password: 61dp6dq38bab1d50921x
- Access the admin panel and delete
carlos.